Pro Evolution Soccer 2010Fans of the Pro Evolution Soccer series will find Pro Evolution Soccer 2010 instantly accessible through the new PS3 games download section. There is no huge overhaul and so there is not learning curve to overcome. This is a definite improvement over last year’s effort with a series of subtle but welcome tweaks.
In this article we are going to offer up some hints and tips to help you get the most from Pro Evolution Soccer 2010.
Editing Names
The argument over Pro Evolution Soccer 2010 versus FIFA Soccer 2010 will rage on & on but one point which continually comes back to bite PES is the fact it lacks all of the official licenses. This means that some teams, & even some players, have been given fake names. If this is a source of irritation for you then you could always access the Edit option from the main menu & update the names yourself. You can change player names, team names, cup names and even stadium names.
The edit feature in Pro Evolution Soccer 2010 is very powerful and you can also create new clubs, players and even new team chants. You can upload your own logos, images for player faces and even sound files to use as chants during the matches. You can also capture your images via the PlayStation Eye Camera if you like.
This may involve a fair bit of work on your part so you’ll be glad to know that you can just download an option file for PES 2010 with all of the correct info from a website. Konami will also be releasing an update soon that tweaks the teams to update the line ups in response to real transfers.
Attacking in PES 2010
The gameplay in Pro Evolution Soccer 2010 has been improved with 360 degrees of movement. You’ll find you can control your players more accurately and the potential for silky footballing moves is vastly increased. As always the main challenge when attacking is to get your player past the defenders & find that killer pass or space to shoot on goal. Let’s take a look at a few moves designed to help you do just that.
The simplest way to get past your man is to sprint using R1.
You can knock the ball further on by tapping R1.
You can keep the ball close & dribble slowly by holding R2 and R1.
You can also press R2 while sprinting to jump over an incoming challenge.
You can perform a Step Over by pressing L1 twice or R2 twice.
You can feint to kick by pressing X when the power gauge is up.
There are various other tricks you can pull off and the majority involve quick changes of direction. It is important to remember that tricks and manoeuvres in PES 2010 are limited by the skill level of the player you are controlling so don’t go attempting elaborate tricks with a big burly defender. You should also try and become familiar with them to the extent that they come out as a natural part of your play because using them in the wrong circumstances will lead to a loss of possession and often a dangerous counter attack.
Defending in PES 2010
Attacking in Pro Evolution Soccer 2010 is relatively easy & very intuitive. Defending is a bit more difficult. For a start you should try to remember to stay in the right position. Blocking is very effective in the game so it is often best to keep your body between the attacker and your goal & avoid actually committing yourself for the tackle. If you get the timing wrong on a challenge then you won’t recover in time to catch the attacker and you will also run the risk of giving away a free kick or penalty. Let’s take a look at some basic defensive moves.
It is good to pressure the ball and it often provokes mistakes in your opposition. The best way to do this is to hold down R1 and X when you don’t have possession.
If you want help closing down an opponent use Square to pull in the nearest man, just be careful you aren’t leaving a gap to be exploited.
You can Slide Tackle with the Circle button but the timing has to be perfect & you must attack the player in possession from the front or you’ll almost certainly be booked.
If an attacker does get past you or the opposition play a long ball into your box then use Triangle to bring your keeper running out. Obviously if you time this wrong your opponent will side step and finish with an easy tap in so be careful!
The most common cheap goal in the game happens when the goalie passes to a nearby defender and the attacker skips in or tackles to break through & score. For inexperienced players I recommend using Circle to kick out with your goalie.
If you win the ball in your own box just hoof it up the field with Square or Circle don’t try to be clever.
Team Set-Up and Tactics
There are two kinds of Pro Evolution Soccer players, some just pick a team and get straight into the action, others like to spend hours tweaking their team line-up, editing player positions and choosing tactics. The majority of teams will be set up automatically with the kind of tactics they tend to play and their top players will be in the first 11 but don’t assume that’s the case. You should definitely check the bench to see if a skilled playmaker or speedy striker is lurking there. You should also change the formation and tactics to suit you.
Another big improvement with Pro Evolution Soccer 2010 is the ratings system. It is now clear how good players are & there is an overall number rating to give you an idea about their strength as well as a detailed breakdown of their specific skills. When you click on a player name in your team line up you can see at a glance what positions they are best employed in. Try tweaking your formation or moving players around and you’ll see their overall rating number change according to how well they can play in the position selected. Remember you don’t just need to stick to the set formations. You can always just edit individual player positions and set the team up exactly how you want it.
You should also remember to set tactics because they make a big difference to how your team plays. You can be defensive or attacking to various degrees or you can choose something like a counter attacking style. There is also a new Card System in PES 2010 which allows you to fine tune the individual roles of each player in your line-up. Just remember it will be superseded by the team tactics you choose.

 r's name should be printed on the PCB (see figure A ). Next, go to the manufacturer's web site. (If you don't know what the URL is, type the company name into the search box at google or
r's name should be printed on the PCB (see figure A ). Next, go to the manufacturer's web site. (If you don't know what the URL is, type the company name into the search box at google or 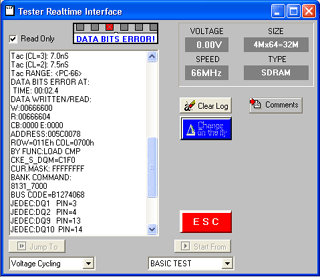



 To make the cables :
To make the cables :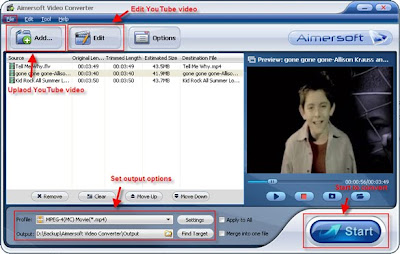
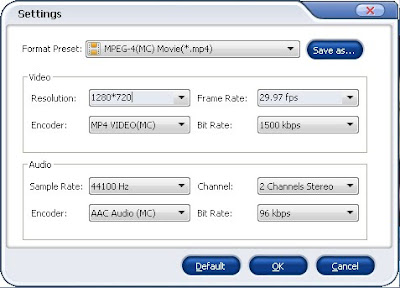
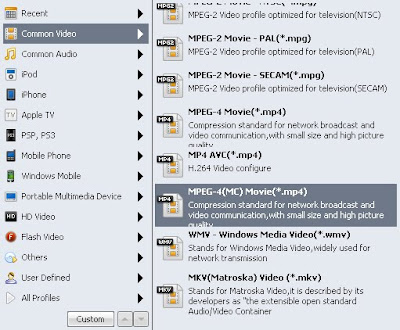 To satisfy your every need, it allows you to configure the resolution, frame rate, bit rate to maintain the high quality of YouTube video.
To satisfy your every need, it allows you to configure the resolution, frame rate, bit rate to maintain the high quality of YouTube video.